WHAT TYPE OF DATA LOSS PREVENTION IS RIGHT FOR YOUR ORGANIZATION?
DATA LOSS PREVENTION BEST PRACTICES
Determine your primary data protection objective. Are you trying to protect your intellectual property, gain more visibility into your data, or meet regulatory compliance? With a main objective in place, it’s easier to determine the most appropriate DLP deployment architecture or combination of architectures. The four main DLP deployment architectures are: Endpoint DLP, Network DLP, Discovery, and Cloud.
DLP is not a security-only decision. If you don’t have an approved budget for a DLP program yet, you need buy-in from other executives like the CFO and the CEO.
Leverage the pain points of different business units to show how DLP can address them. For example, the CFO’s pain points include efficient use of assets and profitable growth. Managed DLP services address these pain points by eliminating the need for additional staff and CapEx to deploy and maintain a DLP program.
When researching DLP vendors, establish your evaluation criteria:
- What types of deployment architectures are offered?
- Do they support Windows, Linux, and OS X with feature parity?
- What deployment options do they offer? Do they provide managed services?
- Do you need to defend against mainly internal or external threats? Or both?
- Do you need to perform content- or context-based inspection and classification? Will your users be able to self-classify documents? Do you need a blend of multiple methods?
- Are you most concerned with protecting structured or unstructured data?
- Do you plan to see and enforce data movement based on policies, events, or users?
- What compliance regulations are you bound by? What new regulations are on the horizon?
- Who are their technology alliance partners and what technologies would you like to integrate with your DLP?
- How quickly do you need to deploy your DLP program?
- Will you need additional staff to manage your DLP program?
Clearly define the roles and responsibilities of the individuals involved in your organization’s DLP program. Building out role-based rights and duties will provide checks and balances.
Start with a clearly defined quick win. Organizations often try complicated initial rollout plans or try to solve too many use cases at once. Define your initial approach and set objectives that are fast and measurable. You should either take the project approach, where you narrow in and focus on a specific data type, or the data visibility approach, where your primary focus is discovery and automated classification of sensitive data to control egress.
Work together with business unit heads to define the DLP policies that will govern your organization’s data. This will help ensure that the different business units are aware of the policies in place and how they might be impacted. Keep in mind that there’s no one right way to develop DLP policies. Often, DLP strategy will align with your corporate culture.
Document your processes carefully. This will help you with consistent application of policies, give you a document of record for when reviews are needed, and will also be helpful when onboarding new team members or employees.
Define success metrics and share reporting with business leaders. Determine the key performance indicators (KPIs) you should measure and monitor them closely to determine the success of your DLP program and areas of improvement. Share these metrics with your organization’s leaders to show the positive impact of DLP and its business value.
DLP is a program, not a product. Installing a DLP tool is just the first step in Data Loss Prevention. While you can get quick wins, understanding that DLP is a program to be continuously worked on will help you achieve lasting success. DLP is a constant process of understanding your data and how users, systems, and events interact with that data to better protect it.
What is VAPT?
VAPT is a term used to describe security testing that is designed to identify and help address cyber security vulnerabilities.
VAPT could include anything from automated vulnerability assessments to human-led penetration testing and red team operations.
“Data is the lifeblood of any organization”
Data or Information was/is the lifeblood of any organization in the past & today and will also remain always. As its volume increases and the threat landscape evolves, taking care of your data is critical, no matter what industry you are in or the size of your company.
As per various research by the individuals/companies, Data Risk and Security Report have revealed that organizations still lack a systematic approach to data security management, which prevents them from ensuring the security of business-critical data and from meeting legislative requirements.
Internet usage has been on the rise for over a decade and according to various researchers/analysts the usage of Ecommerce, Email, and the number of people working remotely has increased significantly.
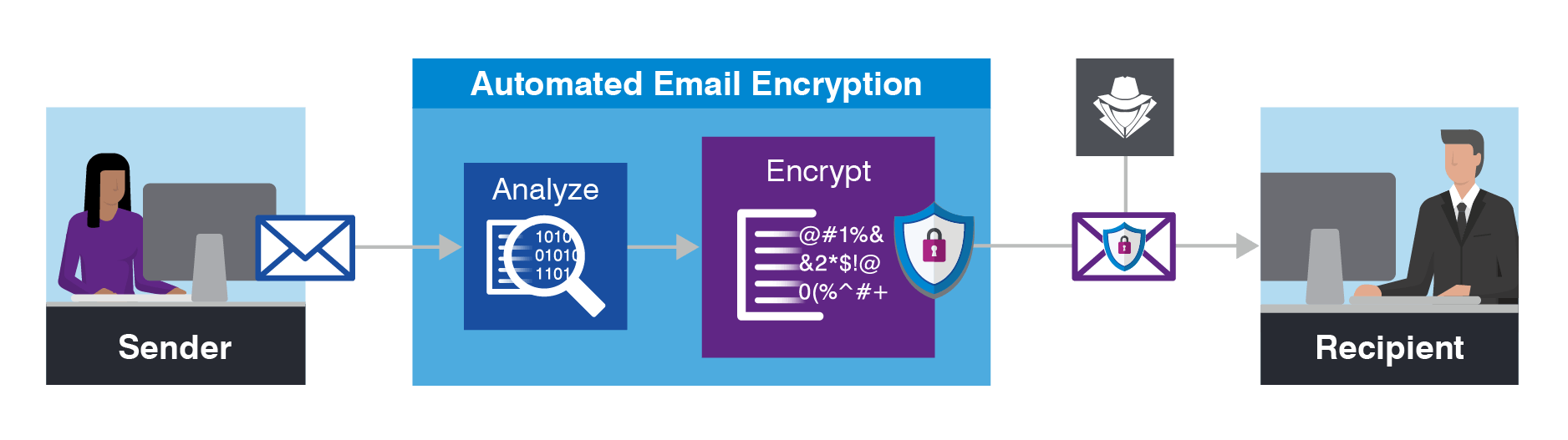
An email has become the modern way of communication & billions of emails send & receive over a net on a daily basis hence 80% & more cyber-attacks began with email as the first line of the attack thus this has created a huge opportunity for the cybercriminals to breach security.
Nowadays the cybercriminals are more professional, well-funded, knowledgeable, Sophisticated, and also more persistent & systematic as compared to few years.
The Cyber attack has a life circle that starts with Impersonation, Business email compromise, and another form of Phishing scams, Malicious insiders and Third parties, etc. which allow cyber criminals to execute Identify Exploitable vulnerability which is the 1st step of the cyber attack life circle.||||| They use Malware fewer files, Downloader, Ransomware, User mistakes, and Steganography, etc. form of the attacks to reach 2nd step of cyber-attack to gain the initial access into the victim system later they strengthen position with victim system.
Once they strengthen their position with the victim system, they start stealing valid user credentials to identify target data/information. These allow cybercriminals for lateral movement and maintain presence into victim networks and package and steal target data to complete the mission.
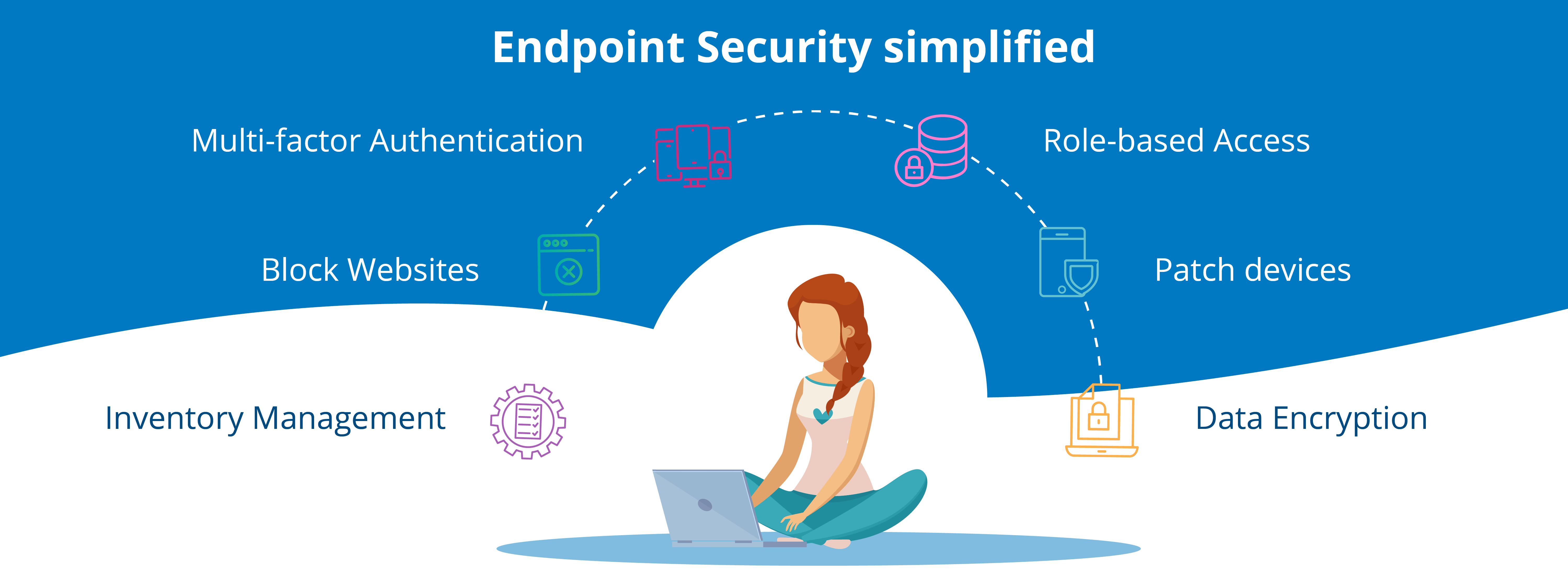
A flexible workplace offer has multiple benefits that allow work from home for the employees, employees on a business trip and remote workers like freelancers and contractors log into the corporate network. Now it’s also common for remote workers to log into your corporate network from their own devices, like Laptop, Mobile & PDA, etc (Now certainly going to increase after this pandemic) which are more likely to have security vulnerabilities. For example, you have little or no ability to ensure that those devices are free from malicious software and that they are properly patched. Also, you are less able to respond promptly if a remote user makes a mistake that leads to unauthorized data access or even data compromise such mistakes not only limited to security breach / weaken that can put your business at risk but also indirect costs caused by damage to your reputation (e.g., loss of customer loyalty and brand value) hence Such mistakes are too costly to ignore.
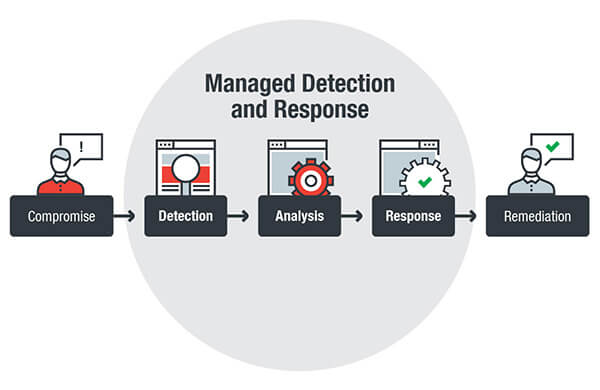
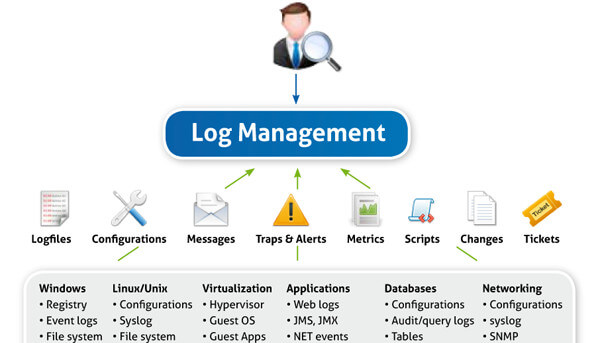
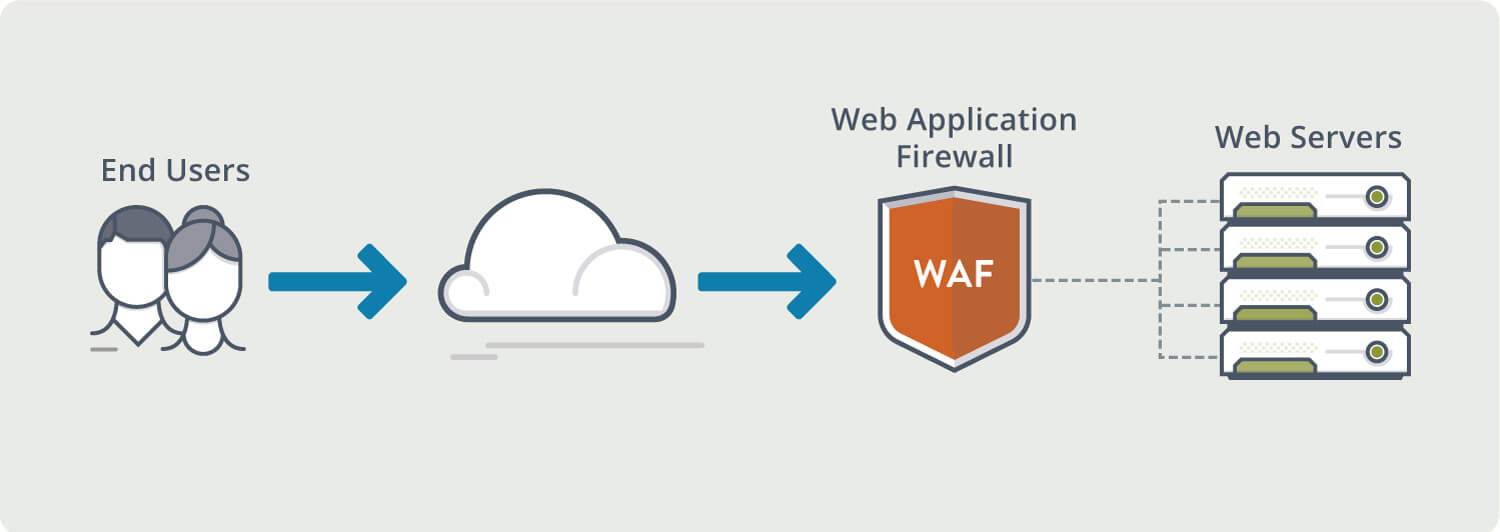
How Now the question raises how to safeguard these Endpoint devices and Networks to avoid any kind of security breach and protect data/information of the organization. To overcome these security challenges, it requires building a layered defense strategy, it’s critical to understand cybersecurity risks and how you intend to reduce them. It’s also important to have a way to measure the business impact of your efforts, so you can ensure you are making appropriate security investments in the security tools like Email Security Gateway, Network Security, Endpoint and Files protection, etc which allow performing activities like Prevention, Detection, Response, hunting Containment, and Analytics, etc.
At B M we design solutions for your data and organization’s security with the help of our highly skilled expertise people and Gartner verified leading products that are highly recommended to an organization for their security.